For this project, you will leverage your research from Project #1 and analysis from Project #2 to develop a risk mitigation strategy for your chosen company. (Amazon)
Project 3 – Risk Mitigation Strategy
Description
For this project, you will leverage your research from Project #1 and analysis from Project #2 to develop
a risk mitigation strategy for your chosen company. The deliverable for this project will be a Risk
Mitigation Strategy that includes a Security Controls Profile based upon the security and privacy controls
catalog from NIST SP 800-53 Revision 5 and the security functions and identifiers from the NIST
Cybersecurity Framework (CSF) Version 1.1.
• NIST SP 800-53 https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-53r5.pdf
• NIST CSF https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.04162018.pdf
Note: Table 2 Framework Core in Appendix A of the NIST Cybersecurity Framework provides a crossreference for each function/category/sub-category to the security and privacy controls from NIST SP
800-53.
Review Guidance for Information Security Functions & Controls
1. Review the NIST Cybersecurity Framework with a particular focus on the Functions, Categories,
and Sub-Categories. Consider how these functions can be employed to mitigate the risks you
identified and documented in Project #2.
2. Review Chapter 2 in Security and Privacy Controls for Information Systems and Organizations
(NIST SP 800-53). Pay special attention to section 2.2 Control Structure and Organization.
3. Review Appendix A in the NIST CSF to identify security Functions/Categories/Sub-Categories
which specifies risk mitigations which could be implemented to reduce or eliminate each risk
listed in your Risk Mitigation Strategy Controls Profile (Table 2).
Develop and Document Your Security Controls Profile
1. Review the sample security controls profile provided in Tables 1 & 2 at the end of this file. Use
this sample to guide your security controls analysis and the formatting of your Risk Mitigation
Strategy Security Controls Profile. The sample entry in Table 2 was derived from the entry shown
below (source: NIST CSF Appendix A Table 2 Framework Core).
2. Copy your Risk Profile (Table 1) from Project #2 into a new file (for your assignment submission).
Then copy the Risk Mitigation Strategy Security Controls Profile (Table #2) from this assignment
file into your project submission file (place it after Table #1). Delete the sample text from Table
#2.
3. Transfer the RISK ID and RISK TITLE columns from Table 1 into Table 2. This is how you will link
your Risk Profile to your Risk Mitigation Strategy. You should have 15 or more risks related to
the company’s business operations, use of the Internet, the company’s IT systems and
infrastructures (including “technologies in use”), and the types and collections of information
used by the company.
4. For each row in your Table 2 (Risk Mitigation Strategy Security Controls Profile), choose a
security function from the NIST CSF which could be implemented to mitigate the identified risk.
Then, review the Category and Sub-Category information for that function. Choose one or more
sub-categories and enter those into your table in the CSF Category ID column.
5. Using the Informative References provided in the NIST CSF Appendix A Table 2: Framework
Core, identify 2 or 3 security controls which, if implemented, will serve to mitigate the specific
risk listed in your risk profile.
6. Write a brief narrative description of the risk mitigation strategy for your identified risk. This
strategy should derive from your selected security function and controls. Use the ABC hallmark
for writing for executive audiences: accuracy, brevity, and clarity.
Develop Your Risk Mitigation Strategy
1. This resource will help you determine what information to include as part of your Risk
Mitigation Strategy for your selected company. https://www.workfront.com/projectmanagement/life-cycle/initiation/business-case
Note: this assignment does not require a full business case. You are not required to provide
financial information, implementation plans, etc. Your presentation of your strategy should
focus on these sections of a business case:
o
o
o
o
o
o
Business problem or opportunity
Benefits
Risk
Technical Solutions
Timescale
Impact on Operations
2. Identify best practices for information security and reasons / justifications for allocating
resources (people, money, technologies) to implement security controls. You will find relevant
best practices and justifications listed in the Executive Summaries and opening chapters of NIST
SP 800-30, NIST SP 800-37, NIST SP 800-53, and the NIST Cybersecurity Framework. You may
wish to discuss your recommendations in terms of timeframe for implementation: immediate,
near-term (6 months?), medium term (12-18 months), within the next two years, etc. Keep in
mind that there may need to be tradeoffs between time and money.
3. Organize your recommendations to formulate your Risk Mitigation Strategy. At a minimum, this
section should include a summary of the business problem (reduce risks related to information
and IT systems and infrastructures), the benefits of implementing security controls, the general
types of risks to be mitigated (focus on the CIA triad), and the policy, processes, and technical
solutions being recommended.
Write
1. An introduction section which provides a brief introduction to the company and the information
/ information technology risks that it faces (you may reuse some of your narrative from Project
#1 and/or Project #2). Your introduction should include a brief overview of the company’s
business operations. Follow this with a description of the purpose and contents of this Risk
Mitigation Strategy deliverable.
2. A separate analysis section in which you present your Risk Profile. Start with a summary of your
Risk Profile. You may reuse your introductory paragraph from Project #2 (revise if necessary)
where you explained your risk profile (what information is contained in the table and what
sources were used to obtain this information). Include a description of the process and
documents used to construct the Risk Profile. Explain the benefits of using a risk profile to help
manage risk. The citations and named documents in this paragraph will serve as citations and
attributions for the contents of Table #1 (bring Table #1 Risk Profile forward from Project #2 and
update if needed). Place Table #1 at the end of this section.
3. A separate analysis section (Security Controls Profile) in which you present your Security
Controls Profile. Provide an introductory paragraph that explains the security controls profile,
e.g., what information is contained in the table and what sources were used to obtain this
information. Describe the process and documents used to construct the Security Controls
Profile.
4. A separate section (Risk Mitigation Strategy) in which you present a high-level strategy for
implementing the risk mitigations (security controls) presented earlier in this deliverable. This
section should include a summary of the business problem (reduce risks related to information
and IT systems and infrastructures), the general types of risks to be mitigated (focus on the CIA
triad and summarize the risks you previously identified), the benefits of implementing security
controls listed in your Security Controls Profile, and the policy, processes, and technical
solutions being recommended for implementation (aligned to your Security Controls Profile).
5. A separate Recommendations and Conclusions section which provides a summary of the
information contained in this deliverable and presents your concluding statements regarding the
business need and business benefits which support implementing your Risk Mitigation Strategy
and the allocation of resources by the company.
Table 1. Risk Profile for [company]
Risk ID
001
002
003
004
005
006
007
008
009
010
011
012
013
014
015
Risk Title
Unauthorized disclosure of
customer information.
Description
Disclosure of or access to customer information must be
restricted to authorized individuals with a need to know.
Unauthorized disclosure or access could result in harm to
customers and financial liabilities for the company.
Risk Category
People
Impact Level
Medium
Table 2. Risk Mitigation Strategy Security Controls Profile
Risk ID
001
002
003
004
005
006
007
008
009
010
011
012
013
014
015
Risk Title
Unauthorized disclosure of
customer information.
Risk Mitigation Strategy
Implementation of role-based access controls
will reduce the risk of unauthorized access to
customer information by controlling which
individuals are granted access to the systems
and software used to collect, process,
transmit, and store this information.
CSF Category ID
PR.AC Identity
Management,
Authentication, and
Access Control: PR.AC4
Security Controls
AC-3 (7) Access
Enforcement | Role
Based Access
Control; AC-3 (11)
Access
Enforcement |
Restrict Access to
Specific
Information Types
1
Company Profile for a Fortune 500: The Case of Amazon
Name:
Institutional Affiliation:
Date:
2
Company Profile for a Fortune 500: The Case of Amazon
Introduction
In recent years, numerous technologies have been developed. However, the increasing
use of these technologies has exposed businesses to various risks and challenges. Such
challenges may affect information security outcomes and undermine resilience against future
threats. Each technology category presents challenges that may have adverse implications for
firms and their customers. This report discusses the case of Amazon. Amazon is a reputable
retailer and technology-oriented firm. Since its establishment, the firm has invested in strategic
technologies to boost its operations and meet the increasing consumer demands. The purpose of
this company profile is to provide a high-level overview of the technologies used and the nature
of the information that needs protection. An overview of the sensitivity level of the information
in the context will be provided.
The company profile
Amazon is an e-commerce firm that was started in 1994. The company is reputable for its
low prices and efficient delivery systems, enabling it to meet the increasing customer needs and
demands. The firm was established by Jeff Bezos, who started as an online bookstore. Since
then, the firm has expanded its operations to include additional products and services (Rikap,
2022). Today, Amazon offers diverse commodities in the e-commerce setting, including
household items, furniture, foodstuff, clothing, electronics, computers, and, but not limited t,
virtual assistance. These services and commodities have enabled the firm to continually deliver
quality interventions focusing more on consumer satisfaction. One major milestone the firm has
reported is transitioning from an online bookstore to a global e-commerce platform (Rikap,
3
2022). This transition enabled the firm to create a complex e-commerce platform informed by
artificial intelligence and machine learning to design a customized consumer experience
(Dhaliwal, 2020). Other milestones relate to the integration of Alexa into its operational models,
the investment in same-day delivery, free shipping, robotic interventions in warehousing
operations, and strategic acquisitions to expand locally and globally (Alimahomed-Wilson &
Reese, 2021).
Amazon operates within the global environment. This setting comprises many external
factors that may influence its operations and success. For example, political stability in the
United States has created a favorable environment for the firm to operate. However, the ongoing
war between Ukraine and Russia has affected the firm’s operations since some suppliers get
products from these countries. Also, the previous trade wars between the United States and
China affected sourcing goods from the latter. Regardless, the majority of the global
environments where the firm operates have recorded stability from a political dimension. Such
stability has favored the firm’s operations and capacity to meet the intended growth goals. Today,
the company operates in the United States and the global environment delivering its services
according to the increasing client demands (Culpepper & Thelen, 2020). The firm is
headquartered in Seattle, Washington, where a majority of its operations are carried out. Amazon
is a publicly traded firm at AMZN on NASDAQ and is classified in the conglomerate industry.
The key people involved in the firm are Jeff Bezos, who is the chairperson, and Andy Jassy, who
is currently the CEO. In 2022, the firm reported operating revenue of $12.25 billion with total
assets of $462.68 billion. The total equity for the firm was $146.04 billion. The company
competes with various players like Walmart and eBay in the retail sector. Also, the firm
competes with entities like Alphabet and IBM in the technology sector. The firm’s stock has
4
reported variations since 2019, with a rise to a peak of 185.97 in 2021 and then a drop to a low of
$84 in 2022. However, the firm has improved its valuation, currently trading at $123.04.
Information technologies used
Amazon has invested in various information technologies like customer relationship
management, enterprise resources planning, and assistance support solutions (Mishra &
Mukherjee, 2019). These systems require strategic user information to help the firm in its
decision-making processes. In this context, it is essential mentioning that the firm’s information
technologies allow it to perform daily operations, including customer management, supplier
handling, and coordinating resources across the global environments. The goal of these
technologies is to create a reliable operating platform where information is shared across the
organizational setting to accomplish better outcomes. Other information systems that the firm
uses include human resources management, accounting, and sales management solutions.
These technologies use various types of information. For example, the firm required
customer information, supplier details, accounting, and employee records to perform its daily
operations. The customer data comprises the information that identifies the clients. This
information may include the customer names, emails, addresses, purchase history, and, but is not
limited to, the payment modes. Customer data is confidential, and the firm processes it by
fulfilling orders and supporting after-sales services. The firm uses information systems like
customer relationship management systems to handle this information. The supplier details
comprise their location, types of products delivered, and but not limited to, their rating from a
performance dimension. Therefore, this information is confidential and should not be shared
against the supplier’s knowledge. This intonation is processed through the inventory management
software and is stored on these information systems. The other information to consider is
5
employee details. Employee records comprise the employment contract, salaries, address, areas
of application, and positions held. This information is confidential since it contains personally
identifiable details. The firm uses this information through the human resources management
systems. The firm also uses information on its financial performance. This information is
processed through the accounting systems. Also, this information is used when the firm intends
to generate annual reports and seasonal highlights of its performance. This information is
available to the public and, therefore, not confidential.
Operational technologies used
The firm uses operational technologies across its facilities. These technologies range
from warehousing robots to product design systems (Delfanti, 2021). Also, the firm uses
machine learning and automation systems to assist it in improving its operations. These systems
require strategic information, including supply chain, inventory, product details, advertising,
pricing, and market insights records. The supply chain data contains details like shipping,
logistics, and customer demand forecasts. This information is contained and processed through
the supply chain management systems and is confidential to the firm. The inventory data
contains information about the warehouse and products in stock. This information is confidential
to the firm and is not available to the public. This information is processed when taking
inventories and stored in the inventory management systems. The product details contain
information like the description, specifications, most preferred customers, and feedback from the
clients. This information is not confidential and is readily available to the public. The
information is processed during sales and is stored on the e-commerce systems.
The advertising data contains information like current marketing strategies, customer
preferences, and impressions. This data is confidential to the firm since it uses it to adjust its
6
strategy and achieve a competitive advantage. This information is contained in the customer
relationship management systems and is used when designing a marketing campaign. The
pricing data contains information like the costs of the products and services and potential
discounts. This information is not confidential and is available to customers. This information is
processed when determining product pricing and stored on the e-commerce platform. The market
insights data contains information about customer feedback and product reviews. This
information is confidential because the firm uses it to optimize its marketing strategies. This
information is processed through benchmark analysis, competition evaluations, and customer
feedback collection. The outcomes are stored in the firm’s sales and marketing systems to inform
the firm’s decisions.
Information use and protection requirements
It is observed that the firm deals with information that define different levels of
confidentiality and privacy. Most information, from the customer and supplier to market insights
and inventory data, is confidential. This information is confidential because it must be protected
from external leaks and exposure. An attack affecting the confidential information described
above may lead to poor market positioning. The attackers may leak confidential information,
including customer records, employee records, and warehousing strategies that the competitors
can replicate. Also, the loss of confidentiality and integrity of the firm’s data may affect its
reputation leading to poor market positioning. These consequences may occur for single and
persistent attacks. Therefore, Amazon must protect this information against external and internal
threats affecting its overall capacity to achieve the intended goals.
Conclusion
7
In this report, an evaluation of the information defining the operations executed by
Amazon has been provided. This data contains details about the firm from an information
management and operational dimension. Most of this information is highly confidential and,
therefore, must be protected to minimize the risks of intrusions and attacks. Failure to protect the
confidential information’s confidentiality, integrity, and availability may lead to one-time or
persistent attacks. Such attacks have adverse effects on the firm and its operations. In this
context, the firm will likely suffer a poor reputation and incur financial losses due to penalties
and fines. Amazon depends on different information assets like customer relationships,
inventory, and supply chain management systems to perform its operations. These systems must
be protected against internal and external threats affecting its operations.
References
8
Alimahomed-Wilson, J., & Reese, E. (2021). The cost of free shipping: Amazon in the global
economy. Pluto Press.
Culpepper, P. D., & Thelen, K. (2020). Are we all Amazon primed? Consumers and the politics
of platform power. Comparative Political Studies, 53(2), 288-318.
Delfanti, A. (2021). The warehouse. Workers and robots at Amazon. Pluto Books.
Dhaliwal, A. (2020). The Rise of Automation and Robotics in Warehouse Management.
In Transforming Management Using Artificial Intelligence Techniques (pp. 63–72). CRC
Press.
Mishra, N., & Mukherjee, S. (2019). Effect of artificial intelligence on customer relationship
management of Amazon in Bangalore. International Journal of Management, 10(4).
Rikap, C. (2022). Amazon: A story of accumulation through intellectual rentiers and predation.
Competition & Change, 26(3-4), pp. 436–466.
Table 1 Summary
9
Category of
Description of the
Information Information
Sensitivity of
How is this
IT
the Information
information used
Assets using
or processed?
or storing
Asset(s)
this
information
Customer
Customer details,
data
purchase history,
Confidential
Order processing
CRM
database
address, email,
payment modes
Supplier
Supplier location,
data
items delivered,
Confidential
Inventory
Inventory
management
management
rating
Employees
Employee records,
data
salary, promotions,
systems
Confidential
Human resources
Employees
operations
database
address, contacts.
Accounting
Financial statements,
financial ratios,
Public
The accounting and The annual
auditing processes
reports,
financial
financial
performance, annual
statements
reports
10
Supply
Suppliers, shipping,
chain
Inventory
Inventory tracking,
Supply chain
and logistical
shipping, and
management
stakeholders
logistical processes
systems
Inventory tracking
Inventory
and warehousing
management
Products, in stock,
Confidential
Confidential
vendors, and
warehouse details
systems
Product
Product description,
details
customer reviews,
web platform
ratings, and
and inventory
specifications
database
Advertising
Customer
and
marketing
Public
Confidential
Sales processes
E-commerce
The customer
CRM and
preferences, ratings,
relationship
sales
and impressions
management
databases
processes
Pricing
Price of products,
Public
discounts
The pricing of
Inventory
products
management
system, ecommerce
platform
Market
Competition,
Insights
Market scanning
CRM
strategic positioning,
and strategic
systems
customer surveys on
planning
feedback
Confidential
11
1
Project 2 –Risk Analysis
Name:
Institutional Affiliation:
Date:
2
Project 2 –Risk Analysis
Introduction
The previous section provided an evaluation of the operations executed by Amazon, Inc.
This report is informed by the need to evaluate the operations that Amazon executed, focusing
more on the prevailing risks and challenges affecting its business and information operations.
Businesses face diverse risks that may affect their operations. Failure to develop a
comprehensive risk management practice may undermine the success achieved in reducing the
threats and their implications on the underlying resources. Information technology risks are
common across the industry due to the continued advancements of the latest innovations. Firms
like Amazon have invested heavily in the latest technologies like e-commerce and robotics
(Maamoun, 2020). These technologies allow the firm to create a comprehensive platform to
support its operations. Amazon remains a reputable firm in the retail industry. However, the
firm’s investments spread across various industries, including the technology sector enabling it to
target diversities consumer markets. The continued investment in these technologies has allowed
the firm to create a reliable operational model for addressing the increasing consumer needs and
demands.
Since its establishment, Amazon has expanded its operations on an international platform
to deliver its products to consumers across the globe. The firm’s success is based primarily on the
ability to enhance service delivery and leverage the latest technologies, including e-commerce,
machine learning, and artificial intelligence (Vähäkainu et al., 2019). The investment in such
technologies has helped Amazon to reduce the delivery and shipment time to the same day,
which gives it a competitive advantage. The firm’s core business operations relate to ecommerce, cloud, and related technologies. Its technologies influence the firm’s operations.
3
These technologies range from e-commerce robotics used in warehouses and information
management solutions (Maamoun, 2020). However, it is essential to mention that the firm faces
different risks. These risks may come from the business operations, information technologies,
and systems used. This report outlines the risks associated with the firm’s information systems
and technologies while determining the need for implementing sufficient security measures. An
overview of the core risks facing the firm from an information systems and technology
dimension.
Analysis
In this section, the primary focus is to create a high-level analysis of the need for
implementing information technology based on the current business operations and solutions
used. The firm is reputable for its investment in the latest technologies. However, these
technologies are associated with weaknesses and vulnerabilities attackers exploit to access
internal information systems and data.
Need for IT security.
Amazon is a large enterprise that deals with customer products and services. The firm has
invested in strategic information technologies to assist it in handling customer information. The
firm’s information solutions help in handling the diverse data elements gathered from the various
segments and markets. For example, the firm involves in handling customer data at the ecommerce platforms. These platforms relate to the core resources that engage the customers
through the sales processes. The core business and technology operations allow the firm to
deliver the associated products and services to the consumers according to their demands
(Babenko & Nehrey, 2021). In handling these tasks, the firm engages the customers through
4
diverse transactions that may be affected by weaknesses like vulnerabilities leading to data loss
(Machete, 2020). For example, Amazon gathers and stores information about its suppliers,
customers, the market, competitors, and but not limited to intellectual property.
Similarly, the firm gathers information about its supply chain operations to optimize
delivery and logistic tasks (De Meyer & Williamson, 2020). It is essential to mention that the
data gathered from these sources is valuable and assists the firm in its daily operations. Data is
considered an essential resource because it generates value for the associated businesses. Firms
today use the information to optimize their operations. This optimization empowers companies
like Amazon to create customized products that match customer needs and expectations. Such
operations create a competitive advantage. Therefore, firms safeguard their information since it
is an essential resource and asset for creating a sustainable competitive advantage.
In the case above, Amazon’s need for information technology security is primarily
informed by the desire to safeguard the data collected. In this context, it is observed that Amazon
gathers information about various areas and resources like customers, the supply chain network,
and products. This information is private to Amazon and, therefore, must be protected against
unauthorized access. Amazon needs such a security plan to provide sufficient protection and
safeguard against unauthorized access. Also, such security resources are preferred because they
provide the ideal protection against exploitation. Attackers continually scan resources like the
AWS platform to identify weaknesses. These weaknesses may direct attackers to internal
resources leading to large-scale data breaches (Rai & Mandoria, 2019). The firm’s information is
sensitive and confidential. Developing a comprehensive information technology security
program may increase awareness about the weaknesses attackers may exploit while guaranteeing
sustainability in protecting internal resources.
5
Sources of threats for the information and business operations
Amazon’s operations include e-commerce, customer payment transactions, warehousing,
shipping, supply chain management, and internal network architectural resources (Machete,
2020). The internal architectural resources comprise interventions like enterprise and other
related information management systems. These information management systems aim to
enhance data handling and processing. These resources are prone to intrusions through data
breaches (Rai & Mandoria, 2019). In recent years, there has been a rise in overall data breaches
affecting the underlying information systems (Rai & Mandoria, 2019). These threats are
associated with the inability to provide a reliable security policy. As mentioned, Amazon’s
business operations include customer relationship management, e-commerce, AWS coordination,
warehousing, and supply chain optimization (Babenko & Nehrey, 2021). Due to the existing
vulnerabilities, these operations are prone to various weaknesses and attacks. For example, the ecommerce platform is prone to intrusion using SQL injection and related strategies. On the same
note, the firm’s AWS platform faces risks like breaches due to weak and insufficient data
encryption. Encryption provides a reliable measure for protecting the integrity of the underlying
information and systems. The absence of sufficient encryption may increase the risks of
successful intrusions.
Another source to consider is the human factor. While Amazon has invested in
information technologies to coordinate its operations, it uses human labor in various areas.
Human capital is prone to attacks due to the underlying vulnerabilities. For example, attackers
target human errors and weaknesses through social engineering. Manipulating human reasoning
and logic increases the risks of intrusions and data breaches since attackers exploit this weakness
to harvest essential credentials. Successful social engineering may lead to identity theft.
6
In the warehousing setting, the firm’s operations are influenced by the potential risks that
may affect its success in guaranteeing efficient machine learning models used to program the
warehousing robots are prone to external intrusions and manipulation (Vähäkainu et al., 2019).
Manipulation of these robots may paralyze the firm’s warehousing operations. For example,
altering the decision-making unit of these robots may affect their capacity to follow the initially
set guidelines and standards to satisfy the needs of the users. The weaknesses exhibited by these
systems are critical since the firm uses robots to optimize its warehousing operations. Operating
with altered robots may increase the shipment duration due to misaligned with the organizational
mission and the customer expectations. Lengthening the shipment and delivery time will likely
affect the firm’s capacity to deal with the increasing competition.
Information and business operations that need protection
The analysis above shows that the company has complex operations that increase the
overall attack vectors that may affect its capacity to guarantee information security. It is
observed that all business operations that relate to information handling and management are
prone to these security risks. In this context, it is observed that operations like e-commerce and
online payment transactions are prone to attacks (Babenko & Nehrey, 2021). Attackers can use
different approaches to hijack customer data, including man-in-the-middle and social
engineering. Complex attacks like ransomware are likely to target internal architectures. Such
vulnerabilities reveal that the firm’s operations need protection against external intrusions and
data breaches.
E-commerce, AWS, online payment transactions, warehousing, supply chain
optimization, and internal data processing units are prone to intrusions and weaknesses. These
7
weaknesses are linked with large-scale data breaches, which may affect the firm’s success in
maintaining a positive customer and market image (Rai & Mandoria, 2019). One observation
made is that these systems and information resources must be protected against internal and
external threats (Babenko & Nehrey, 2021). The core threats arise from the external dimension,
where attackers may exploit vulnerabilities targeting each information operation. For example,
the firm must create a security policy for protecting its customer data against external intrusions
and access. This data is contained in various areas, including the customer database, e-commerce
platform, and the AWS framework. Regardless, the underlying resources must be protected since
they will ensure that the firm maintains the desired levels of integrity and confidentiality
associated with the stored information.
The majority of the insights that are documented in this section come from the corporate
annual reports. The annual reports provide a risk management and assessment segment that
details the challenges likely to face the internal operations from a business and technological
dimension. For example, the annual report reveals that the firm faces risks in areas like legal,
business, information technology, and its core operations (United States Securities and Exchange
Commission, 2021). These risks are classified to determine their impacts on the firm concerning
business operations and sustainability. It is observed that the annual report offers a summary of
the risks facing the business and their potential implications (United States Securities and
Exchange Commission, 2021). The information offered through this source is vital since it is
used as input for developing effective interventions for mitigating the risks and supporting
sustainable practices. Overall, these risks affect the business’s core areas and adversely affect its
information security and operational sustainability. Amazon must, therefore, develop reliable
measures for overcoming these risks to support sustainable operations.
8
The risk profile
The risk profile below represents the primary perils facing Amazon. These risks are
drawn from the various technologies, information systems, and business operations. It is
observed that the ordinary risks revolve around information technologies used in facilitating the
daily business operations for Amazon. For example, the primary risks identified relate to the
firm’s e-commerce platform, AWS resources, warehousing, supply chain, and internal business
operations. Understanding these risks is essential since it offers a high-level overview of their
likelihood of occurrence and impacts on the firm and its business operations. The firm may use
the information gathered to develop an information security policy. The resulting policy should
empower the business with the necessary awareness and resources to mitigate identified risks.
The risks in this context adversely affect Amazon since they reduce its capacity to achieve better
returns. The management team must understand the implications of the risks on the business
from an information and business dimension. It is worth mentioning that these risks can be
mitigated through strategic awareness and investing in the right interventions. Such interventions
may range from employee education and network security measures to restricting third-party
access to the internal architecture in the case of vendors (Li & Xu, 2021).
Ris
k
ID
1
Risk Title
Description
Risk
Category
Technical failure of robots
2
Bias in robotic decisions
3
Privacy concerns in customer
data handling
Robots are prone to failure
Warehousing
due to technical breakdowns
Robots rely on machine
Warehousing
learning algorithms
(Vähäkainu et al., 2019).
These algorithms may
produce biased results.
Machine learning models
Warehousing
may not be best tuned to
accommodate the privacy of
customer and business data.
Impa
ct
Level
High
High
High
9
4
Data exfiltration through
vendor access to inventory
systems
5
The poor security posture of
suppliers
6
Poor vendor relationships
7
Identity theft
8
Security breaches
9
Intrusions through SQL
injections
10
Vendor malpractices
11
Misconfiguration of the AWS
accounts
12
Shadow IT systems and
incompatibility
13
Data loss risks
14
Systems interruptions
Allowing vendors
maximum privileges may
undermine the
confidentiality of
organizational data (Li &
Xu, 2021).
This risk arises from poor
oversight of the security
compliance of systems used
by vendors (Li & Xu,
2021).
A poor supplier relationship
undermines raw materials
delivery.
Identity theft occurs when
attackers steal credentials
belonging to legit
customers.
Security breaches may
occur due to poor security
posture and planning on the
e-commerce platform.
SQL injections likely occur
due to insufficient security
interventions to protect the
website.
Vendors may access
customer data stored on
their cloud resources
without permission.
Poor configuration of the
security of cloud accounts
increases exposure to
unauthorized personnel.
The firm may adopt
multiple undocumented and
unauthorized technologies
within its operational
environments, which may
increase the attack vectors.
Internal systems are at risk
of data loss due to malware
attacks.
System interruptions may
occur due to poor
redundancy planning and
Supply chain
operations
Medi
um
Supply chain
operations
High
Supply chain
operations
High
E-commerce
Medi
um
E-commerce
High
E-commerce
Low
AWS
Medi
um
AWS
High
AWS
Low
Internal
Information
Systems
Internal
Information
Systems
High
High
10
the absence of a backup
solution.
15
Poor data center and systems
optimization
Failure to optimize the data
centers and internal systems
undermines effective
prediction and planning.
Internal
Information
Systems
High
Table 1. The risk profile for Amazon.
Summary and Conclusion
Overall, the risks facing the firm can be classified according to the areas affected. In this
context, the firm’s business and technology operations range from cloud computing to the ecommerce platform. These resources face risks that may affect the company’s sustainability. In
the cloud platform, the firm’s primary risks are breaches, interruption of services, and
malpractices from the vendors. In the e-commerce platform, the core risks facing the firm are
intrusion, security breaches, and identity theft. Most of these risks affect the consumers since
they provide their credentials to receive the associated services. In the warehousing sector, the
firm’s primary risks relate to bias in decision-making activities, potential privacy concerns, and
technical failures. Amazon has invested in robotics to assist in the warehousing operations.
These robots are prone to weaknesses like failures and bias in decision-making. Such risks may
affect the effectiveness of the resulting decisions. Technical failures are expensive and, therefore,
have adverse impacts on the firm concerning supply chain optimization.
Another area to consider is the supply chain management operations. This business
operation requires Amazon to invest in strategic technologies and innovations to optimize
products and service delivery. The company has implemented an integrated system to assist in
11
supply chain operations. In supply chain management, Amazon faces challenges in aligning with
the vendors concerning the information technologies to use. Also, there is a risk of intrusion
through the access that vendors have to the inventory systems. The other risk relates to poor
supplier relationships (Li & Xu, 2021). Poor supplier relationships may affect the supply chain
sustainability due to disruptions of material delivery and a mismatch between demand and
supply.
Enterprise resources and information management systems are other operational areas for
Amazon. The associated technologies are used as a reliable model for ensuring business success.
However, these information systems are faced with risks like data loss, system interruptions, and
poor optimization of the data centers. It is worth mentioning that the risk of misaligned
predictions is linked with insufficient awareness about the best strategies to optimize the data
center and support networks. Also, data breaches may be recorded due to insufficient security
planning and poor engagement of the employees. Likewise, system disruptions may occur due to
poor redundancy planning. These risks have adverse effects on the firm leading to poor sales
prediction, reduced availability of its e-commerce platform, and increased exposure of customer
data to third parties. Such risks may lead to poor alignment of the firm with the prevailing
industry trends, legal litigations, penalties, and fines. Also, addressing these risks may ensure the
firm’s relationship with vendors and customers. Therefore, the firm must develop a model
informed by agencies like the NIST to ensure flexibility in information technology and business
operations risk management.
12
References
Babenko, V., & Nehrey, M. (2021). Complex risk analysis of e-commerce companies related to
COVID-19. The Impact of COVID-19 on E-Commerce, 91-104.
De Meyer, A. C. L., & Williamson, P. J. (2020). Ecosystem edge: Sustaining competitiveness in
the face of disruption.
Li, Y., & Xu, L. (2021). Cybersecurity investments in a two-echelon supply chain with thirdparty risk propagation. International Journal of Production Research, 59(4), 1216–1238.
Maamoun, A. (2020). Shades of Green: Amazon, Walmart, and Retail Sustainability. In SAGE
Business Cases. SAGE Publications: SAGE Business Cases Originals.
Machete, J. M. V. C. D. (2020). Mastercard under threat: measuring the risk of a data
breach (Doctoral dissertation).
Rai, M., & Mandoria, H. (2019). A study on cyber crimes cyber criminals and major security
breaches. Int. Res. J. Eng. Technol, 6(7), 1-8.
United States Securities And Exchange Commission. (2021). AMAZON.COM, INC. United
States Securities And Exchange Commission. Retrieved from
https://d18rn0p25nwr6d.cloudfront.net/CIK-0001018724/f965e5c3-fded-45d3-bbdbf750f156dcc9.pdf
Vähäkainu, P., & Lehto, M. (2019, February). Artificial intelligence in the cyber security
environment. In ICCWS 2019 14th International Conference on Cyber Warfare and
Security: ICCWS 2019 (p. 431). Oxford: Academic Conferences and publishing limited.
1
Project 2 –Risk Analysis
Name:
Institutional Affiliation:
Date:
2
Project 2 –Risk Analysis
Introduction
The previous section provided an evaluation of the operations executed by Amazon, Inc.
This report is informed by the need to evaluate the operations that Amazon executed, focusing
more on the prevailing risks and challenges affecting its business and information operations.
Businesses face diverse risks that may affect their operations.
.
Analysis
In this section, the primary focus is to create a high-level analysis of the need for
implementing information technology based on the current business operations and solutions
used.
Need for IT security.
Amazon is a large enterprise that deals with customer products and services. The firm has
invested in strategic information technologies to assist it in handling customer information.
Sources of threats for the information and business operations
Amazon’s operations include e-commerce, customer payment transactions, warehousing,
shipping, supply chain management, and internal network architectural resources (Machete,
2020).
3
Information and business operations that need protection
The analysis above shows that the company has complex operations that increase the
overall attack vectors that may affect its capacity to guarantee information security.
The risk profile
The risk profile below represents the primary perils facing Amazon. These risks are
drawn from the various technologies, information systems, and business operations. It is
observed that the ordinary risks revolve around information technologies used in facilitating the
daily business operations for Amazon. For example, the primary risks identified relate to the
firm’s e-commerce platform,
Summary and Conclusion
Overall, the risks facing the firm can be classified according to the areas affected. In this
context, the firm’s business and technology operations range from cloud computing to the ecommerce platform.
References
Babenko, V., & Nehrey, M. (2021). Complex risk analysis of e-commerce companies related to
COVID-19. The Impact of COVID-19 on E-Commerce, 91-104.
De Meyer, A. C. L., & Williamson, P. J. (2020). Ecosystem edge: Sustaining competitiveness in
the face of disruption.
4
Li, Y., & Xu, L. (2021). Cybersecurity investments in a two-echelon supply chain with thirdparty risk propagation. International Journal of Production Research, 59(4), 1216–1238.
Maamoun, A. (2020). Shades of Green: Amazon, Walmart, and Retail Sustainability. In SAGE
Business Cases. SAGE Publications: SAGE Business Cases Originals.
Machete, J. M. V. C. D. (2020). Mastercard under threat: measuring the risk of a data
breach (Doctoral dissertation).
Rai, M., & Mandoria, H. (2019). A study on cyber crimes cyber criminals and major security
breaches. Int. Res. J. Eng. Technol, 6(7), 1-8.
United States Securities And Exchange Commission. (2021). AMAZON.COM, INC. United
States Securities And Exchange Commission. Retrieved from
https://d18rn0p25nwr6d.cloudfront.net/CIK-0001018724/f965e5c3-fded-45d3-bbdbf750f156dcc9.pdf
Vähäkainu, P., & Lehto, M. (2019, February). Artificial intelligence in the cyber security
environment. In ICCWS 2019 14th International Conference on Cyber Warfare and
Security: ICCWS 2019 (p. 431). Oxford: Academic Conferences and publishing limited.
1
Company Profile for a Fortune 500: The Case of Amazon
Name:
Institutional Affiliation:
Date:
2
Company Profile for a Fortune 500: The Case of Amazon
Introduction
In recent years, numerous technologies have been developed. However, the increasing
use of these technologies has exposed businesses to various risks and challenges. Such
challenges may affect information security outcomes and undermine resilience against future
threats. Each technology category presents challenges that may have adverse implications for
firms and their customers. This report discusses the case of Amazon. Amazon is a reputable
retailer and technology-oriented firm. Since its establishment, the firm has invested in strategic
technologies to boost its operations and meet the increasing consumer demands. The purpose of
this company profile is to provide a high-level overview of the technologies used and the nature
of the information that needs protection. An overview of the sensitivity level of the information
in the context will be provided.
The company profile
Amazon is an e-commerce firm that was started in 1994. The company is reputable for its
low prices and efficient delivery systems, enabling it to meet the increasing customer needs and
demands. The firm was established by Jeff Bezos, who started as an online bookstore. Since
then, the firm has expanded its operations to include additional products and services (Rikap,
2022). Today, Amazon offers diverse commodities in the e-commerce setting, including
household items, furniture, foodstuff, clothing, electronics, computers, and, but not limited t,
virtual assistance. These services and commodities have enabled the firm to continually deliver
quality interventions focusing more on consumer satisfaction. One major milestone the firm has
reported is transitioning from an online bookstore to a global e-commerce platform (Rikap,
3
2022). This transition enabled the firm to create a complex e-commerce platform informed by
artificial intelligence and machine learning to design a customized consumer experience
(Dhaliwal, 2020). Other milestones relate to the integration of Alexa into its operational models,
the investment in same-day delivery, free shipping, robotic interventions in warehousing
operations, and strategic acquisitions to expand locally and globally (Alimahomed-Wilson &
Reese, 2021).
Amazon operates within the global environment. This setting comprises many external
factors that may influence its operations and success. For example, political stability in the
United States has created a favorable environment for the firm to operate. However, the ongoing
war between Ukraine and Russia has affected the firm’s operations since some suppliers get
products from these countries. Also, the previous trade wars between the United States and
China affected sourcing goods from the latter. Regardless, the majority of the global
environments where the firm operates have recorded stability from a political dimension. Such
stability has favored the firm’s operations and capacity to meet the intended growth goals. Today,
the company operates in the United States and the global environment delivering its services
according to the increasing client demands (Culpepper & Thelen, 2020). The firm is
headquartered in Seattle, Washington, where a majority of its operations are carried out. Amazon
is a publicly traded firm at AMZN on NASDAQ and is classified in the conglomerate industry.
The key people involved in the firm are Jeff Bezos, who is the chairperson, and Andy Jassy, who
is currently the CEO. In 2022, the firm reported operating revenue of $12.25 billion with total
assets of $462.68 billion. The total equity for the firm was $146.04 billion. The company
competes with various players like Walmart and eBay in the retail sector. Also, the firm
competes with entities like Alphabet and IBM in the technology sector. The firm’s stock has
4
reported variations since 2019, with a rise to a peak of 185.97 in 2021 and then a drop to a low of
$84 in 2022. However, the firm has improved its valuation, currently trading at $123.04.
Information technologies used
Amazon has invested in various information technologies like customer relationship
management, enterprise resources planning, and assistance support solutions (Mishra &
Mukherjee, 2019). These systems require strategic user information to help the firm in its
decision-making processes. In this context, it is essential mentioning that the firm’s information
technologies allow it to perform daily operations, including customer management, supplier
handling, and coordinating resources across the global environments. The goal of these
technologies is to create a reliable operating platform where information is shared across the
organizational setting to accomplish better outcomes. Other information systems that the firm
uses include human resources management, accounting, and sales management solutions.
These technologies use various types of information. For example, the firm required
customer information, supplier details, accounting, and employee records to perform its daily
operations. The customer data comprises the information that identifies the clients. This
information may include the customer names, emails, addresses, purchase history, and, but is not
limited to, the payment modes. Customer data is confidential, and the firm processes it by
fulfilling orders and supporting after-sales services. The firm uses information systems like
customer relationship management systems to handle this information. The supplier details
comprise their location, types of products delivered, and but not limited to, their rating from a
performance dimension. Therefore, this information is confidential and should not be shared
against the supplier’s knowledge. This intonation is processed through the inventory management
software and is stored on these information systems. The other information to consider is
5
employee details. Employee records comprise the employment contract, salaries, address, areas
of application, and positions held. This information is confidential since it contains personally
identifiable details. The firm uses this information through the human resources management
systems. The firm also uses information on its financial performance. This information is
processed through the accounting systems. Also, this information is used when the firm intends
to generate annual reports and seasonal highlights of its performance. This information is
available to the public and, therefore, not confidential.
Operational technologies used
The firm uses operational technologies across its facilities. These technologies range
from warehousing robots to product design systems (Delfanti, 2021). Also, the firm uses
machine learning and automation systems to assist it in improving its operations. These systems
require strategic information, including supply chain, inventory, product details, advertising,
pricing, and market insights records. The supply chain data contains details like shipping,
logistics, and customer demand forecasts. This information is contained and processed through
the supply chain management systems and is confidential to the firm. The inventory data
contains information about the warehouse and products in stock. This information is confidential
to the firm and is not available to the public. This information is processed when taking
inventories and stored in the inventory management systems. The product details contain
information like the description, specifications, most preferred customers, and feedback from the
clients. This information is not confidential and is readily available to the public. The
information is processed during sales and is stored on the e-commerce systems.
The advertising data contains information like current marketing strategies, customer
preferences, and impressions. This data is confidential to the firm since it uses it to adjust its
6
strategy and achieve a competitive advantage. This information is contained in the customer
relationship management systems and is used when designing a marketing campaign. The
pricing data contains information like the costs of the products and services and potential
discounts. This information is not confidential and is available to customers. This information is
processed when determining product pricing and stored on the e-commerce platform. The market
insights data contains information about customer feedback and product reviews. This
information is confidential because the firm uses it to optimize its marketing strategies. This
information is processed through benchmark analysis, competition evaluations, and customer
feedback collection. The outcomes are stored in the firm’s sales and marketing systems to inform
the firm’s decisions.
Information use and protection requirements
It is observed that the firm deals with information that define different levels of
confidentiality and privacy. Most information, from the customer and supplier to market insights
and inventory data, is confidential. This information is confidential because it must be protected
from external leaks and exposure. An attack affecting the confidential information described
above may lead to poor market positioning. The attackers may leak confidential information,
including customer records, employee records, and warehousing strategies that the competitors
can replicate. Also, the loss of confidentiality and integrity of the firm’s data may affect its
reputation leading to poor market positioning. These consequences may occur for single and
persistent attacks. Therefore, Amazon must protect this information against external and internal
threats affecting its overall capacity to achieve the intended goals.
Conclusion
7
In this report, an evaluation of the information defining the operations executed by
Amazon has been provided. This data contains details about the firm from an information
management and operational dimension. Most of this information is highly confidential and,
therefore, must be protected to minimize the risks of intrusions and attacks. Failure to protect the
confidential information’s confidentiality, integrity, and availability may lead to one-time or
persistent attacks. Such attacks have adverse effects on the firm and its operations. In this
context, the firm will likely suffer a poor reputation and incur financial losses due to penalties
and fines. Amazon depends on different information assets like customer relationships,
inventory, and supply chain management systems to perform its operations. These systems must
be protected against internal and external threats affecting its operations.
References
8
Alimahomed-Wilson, J., & Reese, E. (2021). The cost of free shipping: Amazon in the global
economy. Pluto Press.
Culpepper, P. D., & Thelen, K. (2020). Are we all Amazon primed? Consumers and the politics
of platform power. Comparative Political Studies, 53(2), 288-318.
Delfanti, A. (2021). The warehouse. Workers and robots at Amazon. Pluto Books.
Dhaliwal, A. (2020). The Rise of Automation and Robotics in Warehouse Management.
In Transforming Management Using Artificial Intelligence Techniques (pp. 63–72). CRC
Press.
Mishra, N., & Mukherjee, S. (2019). Effect of artificial intelligence on customer relationship
management of Amazon in Bangalore. International Journal of Management, 10(4).
Rikap, C. (2022). Amazon: A story of accumulation through intellectual rentiers and predation.
Competition & Change, 26(3-4), pp. 436–466.
Table 1 Summary
9
Category of
Description of the
Information Information
Sensitivity of
How is this
IT
the Information
information used
Assets using
or processed?
or storing
Asset(s)
this
information
Customer
Customer details,
data
purchase history,
Confidential
Order processing
CRM
database
address, email,
payment modes
Supplier
Supplier location,
data
items delivered,
Confidential
Inventory
Inventory
management
management
rating
Employees
Employee records,
data
salary, promotions,
systems
Confidential
Human resources
Employees
operations
database
address, contacts.
Accounting
Financial statements,
financial ratios,
Public
The accounting and The annual
auditing processes
reports,
financial
financial
performance, annual
statements
reports
10
Supply
Suppliers, shipping,
chain
Inventory
Inventory tracking,
Supply chain
and logistical
shipping, and
management
stakeholders
logistical processes
systems
Inventory tracking
Inventory
and warehousing
management
Products, in stock,
Confidential
Confidential
vendors, and
warehouse details
systems
Product
Product description,
details
customer reviews,
web platform
ratings, and
and inventory
specifications
database
Advertising
Customer
and
marketing
Public
Confidential
Sales processes
E-commerce
The customer
CRM and
preferences, ratings,
relationship
sales
and impressions
management
databases
processes
Pricing
Price of products,
Public
discounts
The pricing of
Inventory
products
management
system, ecommerce
platform
Market
Competition,
Insights
Market scanning
CRM
strategic positioning,
and strategic
systems
customer surveys on
planning
feedback
Confidential
11
1
Company Profile for a Fortune 500: The Case of Amazon
Name:
Institutional Affiliation:
Date:
2
Company Profile for a Fortune 500: The Case of Amazon
Introduction
In recent years, numerous technologies have been developed. However, the increasing
use of these technologies has exposed businesses to various risks and challenges. Such
challenges may affect information security outcomes and undermine resilience against future
threats. Each technology category presents challenges that may have adverse implications for
firms and their customers.
The company profile
Amazon is an e-commerce firm that was started in 1994. The company is reputable for its
low prices and efficient delivery systems, enabling it to meet the increasing customer needs and
demands.
Information technologies used
Amazon has invested in various information technologies like customer relationship
management, enterprise resources planning, and assistance support solutions (Mishra &
Mukherjee, 2019). These systems require strategic user information to help the firm in its
decision-making processes.
Information use and protection requirements
It is observed that the firm deals with information that define different levels of
confidentiality and privacy. Most information, from the customer and supplier to market insights
and inventory data, is confidential.
Conclusion
3
In this report, an evaluation of the information defining the operations executed by
Amazon has been provided. This data contains details about the firm from an information
management and operational dimension
References
Alimahomed-Wilson, J., & Reese, E. (2021). The cost of free shipping: Amazon in the global
economy. Pluto Press.
Culpepper, P. D., & Thelen, K. (2020). Are we all Amazon primed? Consumers and the politics
of platform power. Comparative Political Studies, 53(2), 288-318.
Delfanti, A. (2021). The warehouse. Workers and robots at Amazon. Pluto Books.
Dhaliwal, A. (2020). The Rise of Automation and Robotics in Warehouse Management.
In Transforming Management Using Artificial Intelligence Techniques (pp. 63–72). CRC
Press.
Mishra, N., & Mukherjee, S. (2019). Effect of artificial intelligence on customer relationship
management of Amazon in Bangalore. International Journal of Management, 10(4).
4
Rikap, C. (2022). Amazon: A story of accumulation through intellectual rentiers and predation.
Competition & Change, 26(3-4), pp. 436–466.
Table 1 Summary
Category of
Description of the
Information Information
Sensitivity of
How is this
IT
the Information
information used
Assets using
or processed?
or storing
Asset(s)
this
information
Customer
Customer details,
data
purchase history,
address, email,
payment modes
Confidential
Order processing
CRM
database
5
Supplier
Supplier location,
data
items delivered,
Confidential
Inventory
Inventory
management
management
rating
Employees
Employee records,
data
salary, promotions,
systems
Confidential
Human resources
Employees
operations
database
address, contacts.
Accounting
Financial statements,
Public
financial ratios,
The accounting and The annual
auditing processes
reports,
financial
financial
performance, annual
statements
reports
Supply
Suppliers, shipping,
chain
Inventory
Inventory tracking,
Supply chain
and logistical
shipping, and
management
stakeholders
logistical processes
systems
Inventory tracking
Inventory
and warehousing
management
Products, in stock,
Confidential
Confidential
vendors, and
warehouse details
systems
Product
Product description,
Public
Sales processes
E-commerce
details
customer reviews,
web platform
ratings, and
and inventory
specifications
database
6
Advertising
Customer
and
marketing
Confidential
The customer
CRM and
preferences, ratings,
relationship
sales
and impressions
management
databases
processes
Pricing
Price of products,
Public
discounts
The pricing of
Inventory
products
management
system, ecommerce
platform
Market
Competition,
Insights
Market scanning
CRM
strategic positioning,
and strategic
systems
customer surveys on
planning
feedback
Confidential
Essay Writing Service Features
Our Experience
No matter how complex your assignment is, we can find the right professional for your specific task. Achiever Papers is an essay writing company that hires only the smartest minds to help you with your projects. Our expertise allows us to provide students with high-quality academic writing, editing & proofreading services.
Free Features
Free revision policy
$10Free bibliography & reference
$8Free title page
$8Free formatting
$8How Our Dissertation Writing Service Works
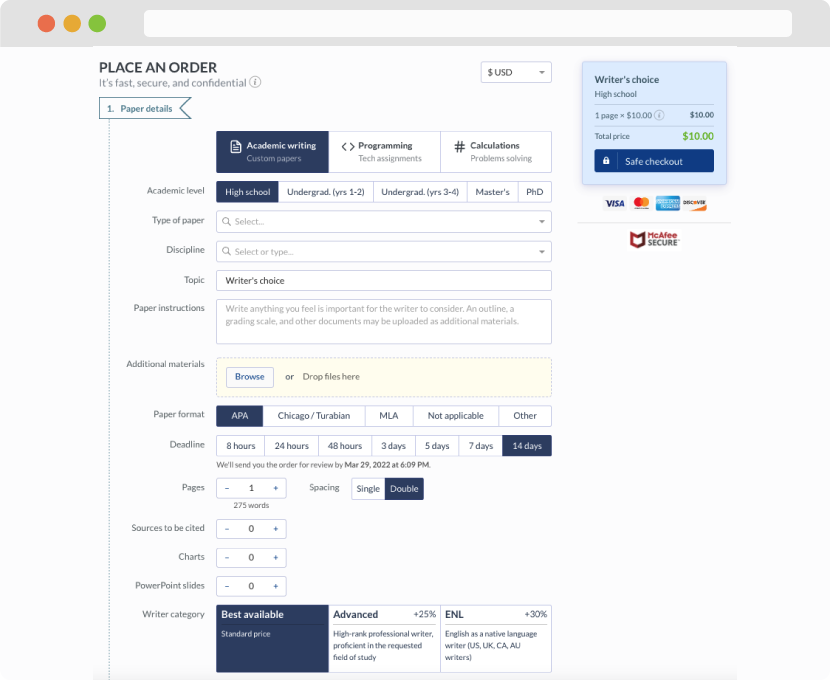
First, you will need to complete an order form. It's not difficult but, if anything is unclear, you may always chat with us so that we can guide you through it. On the order form, you will need to include some basic information concerning your order: subject, topic, number of pages, etc. We also encourage our clients to upload any relevant information or sources that will help.
Complete the order form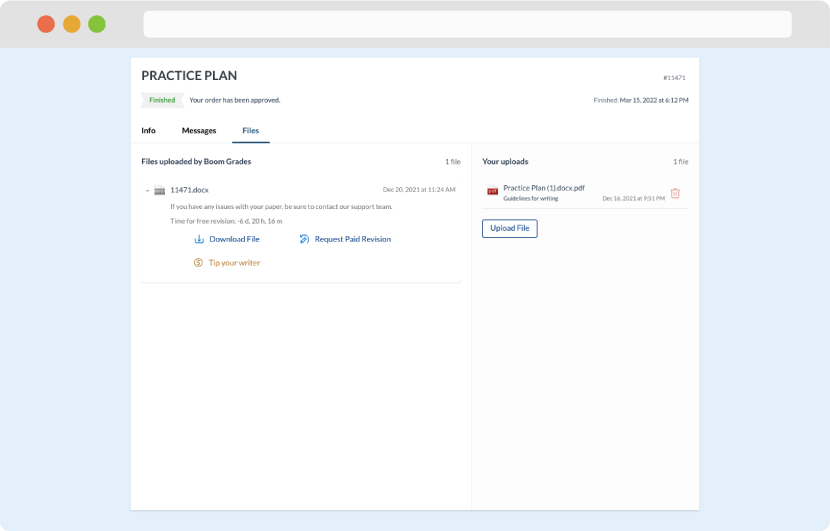
Once we have all the information and instructions that we need, we select the most suitable writer for your assignment. While everything seems to be clear, the writer, who has complete knowledge of the subject, may need clarification from you. It is at that point that you would receive a call or email from us.
Writer’s assignment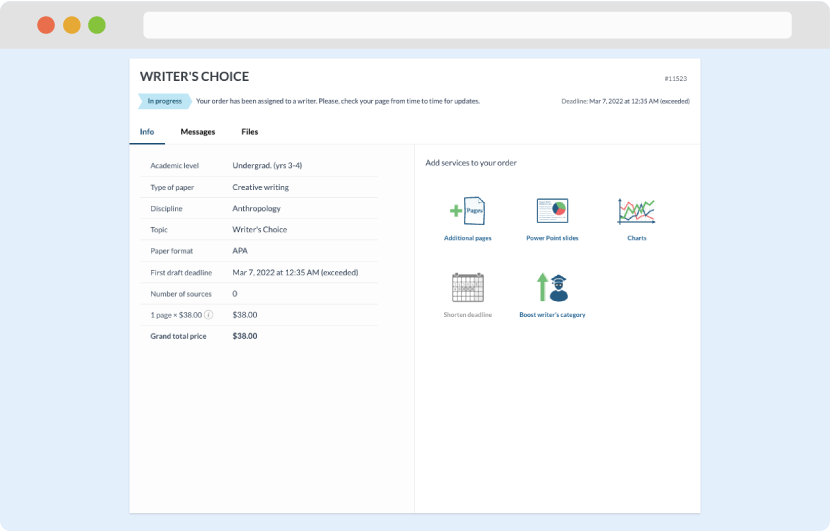
As soon as the writer has finished, it will be delivered both to the website and to your email address so that you will not miss it. If your deadline is close at hand, we will place a call to you to make sure that you receive the paper on time.
Completing the order and download