Identify one issue from the weekly reading and create a Legal Issue Brief.
Privacy and Data Protection
in Cyberspace
LAW 402: LAW OF E-COMMERCE
UPON COMPLETION OF THIS WEEK’S
ACTIVITIES, YOU WILL BE ABLE TO:
•Identify and explain several ways antitrust laws
have been applied to online activities.
•Describe laws that protect privacy in
cyberspace.
•Interpret and summarize common security
issues that arise in an e-commerce transaction.
PRIVACY
•Privacy means different things to different individuals and in
different contexts.
•Its importance varies from individual to individual, community to
community, organization to organization and government to
government.
•Technology combined with social, economic and political factors has
raised concerns for those concerned with government, enterprise
and personal freedom.
INFORMATION FREEDOM
•Freedom of expression and communication of ideas has
been deemed a universal human right.
•The right to privacy and the confidentiality of
communications in addition to protection of honor must
also be protected.
•Electronic communication and storage of data have greatly
impacted these rights.
DIGITAL DATA STORAGE
•Gone are the days of paper data storage and
consideration of practicality issues regarding the
amount of room needed to store data.
•Digital Age: data can be stored in operating systems.
•Ease of storage allows public and private bodies to
collect and store a larger amount of data (and
personal information) than ever before.
TWO TYPES OF PRIVACY:
1. Information privacy: refers to the ways in which information is
gathered, recorded, accessed and released.
• The multitude of recording and storage options has become
a serious issue for regulation and control
2. Personal privacy: refers to privacy of the person
• Can be invaded by those seeking to photograph, film and
record in public and private places
ELECTRONIC RECORDING AND PRIVACY
REGULATION
•OECD guidelines noted that the increase in international data
transmission has made it necessary to address privacy in relation to
personal data.
• require that personal information cannot be collected unless the
person concerned consents or is informed of why it is being
collected, who will use it, and in what way it will be used.
DATA PROTECTION
Australian Telecommunications Act 1997 prohibits carriers,
carriage service providers and others of disclosing
information obtained as a result of normal business
activities yet requires carriers to have wiretapping
capabilities in place for ‘lawful’ surveillance.
PRIVACY ABUSE
An increase in the amount of data collected and
stored also leads to an increase in mistakes.
•There have been numerous incidents where privacy
has been invaded and wrongful information made
public at the expense of the individual’s integrity. To
name a few incidents resulting from privacy abuse,
it has caused wrongful lawsuits, loss of
employment, false allegations against reputation.
COOKIES
A process where information from personal computers is
sent to the hosts of websites visited.
• a small text file placed on the user’s hard drive, often
without the user’s knowledge, acting like an
identification card but cannot be executed as code or
transmit viruses.
WEB BUGS
Objects embedded in web pages or email used to
monitor use.
•Provide the IP address of the computer that
procured the web bug, the URL of the web page
with the web bug, the URL of the web bug image
and the date the web bug was viewed in addition
to the type and version of the browser and any
cookie information related to the website where
the bug was located.
As cyberspace grows at a
prodigious rate, so does the
potential for privacy abuse.
Minimization of future privacy abuse entails
monitoring changes occurring in national and
international legal environments.
REGULATIONS IN CYBERSPACE
Should progress in a way that includes national
governance with respect to fundamental human
rights. They should also respect human diversity
with respect to global values.
Essay Writing Service Features
Our Experience
No matter how complex your assignment is, we can find the right professional for your specific task. Achiever Papers is an essay writing company that hires only the smartest minds to help you with your projects. Our expertise allows us to provide students with high-quality academic writing, editing & proofreading services.
Free Features
Free revision policy
$10Free bibliography & reference
$8Free title page
$8Free formatting
$8How Our Dissertation Writing Service Works
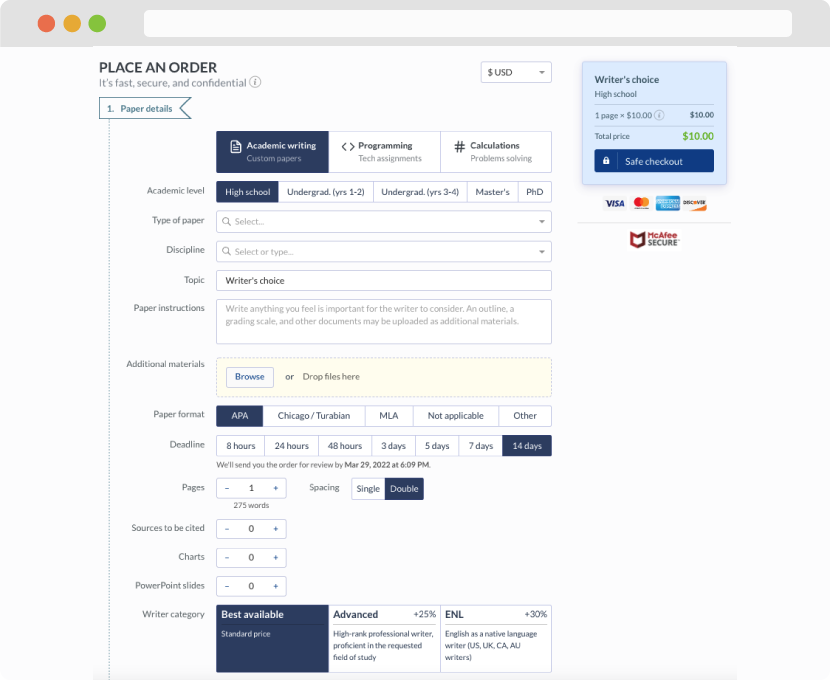
First, you will need to complete an order form. It's not difficult but, if anything is unclear, you may always chat with us so that we can guide you through it. On the order form, you will need to include some basic information concerning your order: subject, topic, number of pages, etc. We also encourage our clients to upload any relevant information or sources that will help.
Complete the order form
Once we have all the information and instructions that we need, we select the most suitable writer for your assignment. While everything seems to be clear, the writer, who has complete knowledge of the subject, may need clarification from you. It is at that point that you would receive a call or email from us.
Writer’s assignment
As soon as the writer has finished, it will be delivered both to the website and to your email address so that you will not miss it. If your deadline is close at hand, we will place a call to you to make sure that you receive the paper on time.
Completing the order and download