Chapter 1 provided a high-level overview of the Information Systems Security Policy Management:
Information Systems Security (ISS). What is it? The act of protecting information and the systems that store, process and transmit
Why is ISS needed? ISS provides a foundation for establishing protection of systems and data against risks such as: Unauthorized access and Use, Disclosure, System Disruption, Modification or Corruption
Destruction
After reading chapter 1 and looking at the ISS Management Life Cycle.
Let’s look at a real-world scenario and discuss what C-I-A Triad is all about.
You must do the following:
1) Create a new thread. As indicated above, please explain how DHS should handle the situation described in the preceding paragraph.
Security Policies and Implementation Issues
Lesson
1
Information Systems Security Policy Management
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Page ‹#›
Security Policies and Implementation Issues
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
1
Information Systems Security (ISS)
The act of protecting information and the systems that store and process it
The protection is against risks that would lead to:
Unauthorized access
Use
Disclosure
Disruption
Modification
Destruction
Page ‹#›
Security Policies and Implementation Issues
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
8/30/2016
2
ISS Management Life Cycle
Page ‹#›
Security Policies and Implementation Issues
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
8/30/2016
3
ISS Management Life Cycle
Page ‹#›
Security Policies and Implementation Issues
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
8/30/2016
4
Align, Plan, and Organize
What do you want to do?
Build, Acquire, and Implement
Schedules
Builds
Deliver, Service, and Support
Minimize threats
Monitor, Evaluate, and Assess
How do you want to get there?
Deliverables
Operational management and support
Test and monitor controls
Analyze effectiveness
Auditing
Analyze data
SLAs
Align, Plan, and Organize: Key Concepts
Page ‹#›
Security Policies and Implementation Issues
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
8/30/2016
5
Threat
A human-caused or natural event that could impact the system
Vulnerability
Risk
A weakness in a system that can be exploited
The likelihood or probability of an event and its impact
Audits
Page ‹#›
Security Policies and Implementation Issues
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
8/30/2016
6
Self-Assessment
This is typically in the form of quality assurance (QA) and quality control (QC).
External Audit
Regulator Audit
Internal Audit
This consists of reports to the board of directors and assesses the business.
This is done by an outside firm hired by the company to validate internal audit work and perform special assessment, such as certifying annual financial statements.
This is an audit by government agencies that assess the company’s compliance with laws and regulations.
Information Assurance (IA)
Page ‹#›
Security Policies and Implementation Issues
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Nonrepudiation is the assurance that someone cannot deny something. Typically, nonrepudiation refers to the ability to ensure that a party to a contract or a communication cannot deny the authenticity of their signature on a document or the sending of a message that they originated.
8/30/2016
7
IA
Confidentiality
Integrity
Availability
Authentication
Nonrepudiation
C-I-A Triad
Page ‹#›
Security Policies and Implementation Issues
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
8/30/2016
8
Information Security Governance
Page ‹#›
Security Policies and Implementation Issues
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
8/30/2016
9
Information Security Governance
Risk Assessment
Security Policy Framework
Compliance
Information Assurance
Security Policy Framework Components
Page ‹#›
Security Policies and Implementation Issues
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
8/30/2016
10
Standards
Procedures
Guidelines
Defines how an organization performs and conducts business functions and transactions with a desired outcome
Established methods implemented organization-wide
Steps required to implement a process
Parameters within which a policy, standard, or procedure is suggested
Policy
Definitions
Statements that define terms used in policy documents and set context in which policy documents are interpreted
Principle
Establishes tone at the top and authority by which policies are enforced
Foundational Reasons for Using and Enforcing Security Policies
Page ‹#›
Security Policies and Implementation Issues
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
8/30/2016
11
Protecting systems from insider threats
Protecting information at rest and in transit
Controlling change to IT infrastructure
Defending the business
Roles of Security Policies in an Organization
Maintenance of a secure work environment
Change controls
Physical security
Protection of information resources
Insider threats
At rest and in transit
Page ‹#›
Security Policies and Implementation Issues
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
8/30/2016
12
Importance of IS Security Policies
Page ‹#›
Security Policies and Implementation Issues
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
8/30/2016
13
With ISS Policies
Data Protection
Change Control
Risk Management
Insider Threat Protection
Increased Availability
Without ISS Policies
Higher Cost
Regulatory Non-Compliance
Vulnerability to Mishandling
Vulnerability to Attack
Business Drivers
Security policies should be relevant to business needs
Security controls should be compatible with business requirements
Business concerns
Cost: What is the cost of controls?
Impact: What is the impact on customers?
Regulation: Does the organization have a legally defensible position?
Adoption: Do employees understand the policies and controls? Are employees willing to follow the policies and controls?
Page ‹#›
Security Policies and Implementation Issues
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
8/30/2016
14
What Is Compliance?
Adhering to rules, such as
Security policies
Industry regulations
Laws
With regards to information security, security policies take regulatory/legal requirements into account
Page ‹#›
Security Policies and Implementation Issues
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
8/30/2016
15
Security Policy Compliance
Relationship exists between controls and policy
Controls support policy
Compliance is measured against
controls
Policy supports business
requirements
Business requirements derived
from regulatory requirements
Page ‹#›
Security Policies and Implementation Issues
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
8/30/2016
16
Regulatory Requirements
Business Requirements
Policies
Controls
Policy vs. Controls
Page ‹#›
Security Policies and Implementation Issues
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
8/30/2016
17
Policy
What type of protection
Why protections are needed
Controls
How protections are to be implemented – the technical details
Security Control Classifications
Page ‹#›
Security Policies and Implementation Issues
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
8/30/2016
18
Physical
Devices that prevent or deter access
Locks, cameras, guards
Administrative/
Procedural
Controls that require human effort
Security awareness training, operations manuals
Technical
Logical controls imposed through software
Passwords, anti-malware software
Security Control Actions
Page ‹#›
Security Policies and Implementation Issues
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
8/30/2016
19
Security Control Design Types
Page ‹#›
Security Policies and Implementation Issues
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
8/30/2016
20
Preventative
Prevents an incident from occurring
Example: Firewalls
Detective
Alerts the organization to the threat
Example: Log review
Corrective
Restores operations
Example: Backup and recovery
Mitigating Risk Exposure Through Policies
Policy reflects business risk management decisions and perception of risk by:
Promoting risk-aware culture through employee security awareness program
Preventing intellectual property (IP) loss in concurrence with human resources (HR) policies
Policy compliance equates to an acceptable level of risk (risk appetite)
Page ‹#›
Security Policies and Implementation Issues
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
8/30/2016
21
Minimizing Liability through Policy Implementation
Page ‹#›
Security Policies and Implementation Issues
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
8/30/2016
22
Create or Update Policy
Enforce Policy
Respond to Incidents
Analyze Incidents
Educate Employees
Protecting Intellectual Property (IP)
Broad term covering original information owned that provides a business advantage
Ideas, products, inventions
Business processes, business models
Classify and label data
Sensitive, Confidential, etc.
Mark files when possible
Protect digital assets
Files, graphics, audio, video, etc.
Take regular inventory
Page ‹#›
Security Policies and Implementation Issues
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
8/30/2016
23
Protecting Digital Assets
Page ‹#›
Security Policies and Implementation Issues
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
8/30/2016
24
Personally Identifiable Information
This category of data may need special treatment due to:
Customer expectations of privacy
Legal requirements
Laws may vary by state or industry
Security policy should address:
Disclosure to individuals (what is being stored and how it is used)
Encryption of PII in transmission and/or at rest
Page ‹#›
Security Policies and Implementation Issues
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
8/30/2016
25
Minimizing Business Liability
Liability arises when the organization fails to meet its obligations
Example: Legal or contractual requirements
Impacts
Fines
Restriction of business
Lost business through lost of customer trust
Lawsuits
Good security policies reduce liability
Page ‹#›
Security Policies and Implementation Issues
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
8/30/2016
26
Tools to Reduce Business Liability
Acceptable Use Policies (AUPs)
Guidelines for employee behavior
Confidentiality Agreements
Prohibits entities (employees, contractors, business partners, etc.) from disclosing confidential, sensitive or proprietary information
Insurance Policies
Transfer of risk in the event of an incident
Page ‹#›
Security Policies and Implementation Issues
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
8/30/2016
27
Reducing Risk through Operational Consistency
Business processes should be repeatable and sustainable to support:
Better risk detection and removal
Operational efficiency
Through policies, organizations can:
Enforce business processes
Reduce operational deviation
Page ‹#›
Security Policies and Implementation Issues
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
8/30/2016
28
Policy Oversight
Is policy achieving the desired results?
Policy should state oversight requirements
Includes:
Identification of measurements
Reporting
requirements
Page ‹#›
Security Policies and Implementation Issues
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
8/30/2016
29
Improving
Measuring
Reviewing
Tracking
Monitoring
Managing Operational Deviation
Some deviation is inevitable and may be acceptable
Exception (waiver) processes
Determine necessity of deviations (e.g., benefit to business)
Analyze and mitigate residual risk
Provide a formal approval process
Document approved deviations
Page ‹#›
Security Policies and Implementation Issues
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
8/30/2016
30
Roles and Responsibilities
Page ‹#›
Security Policies and Implementation Issues
© 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company
www.jblearning.com
All rights reserved.
Chief Privacy Officer
Identifies legal requirements for PII
Executive and Senior Management
Identifies business drivers
Implements and enforces policy
Human Resources Department
Consults on possible conflicts between HR policy and security policies
Information Technology Staff
Implements security controls
Legal Department
Reviews draft policy statements
8/30/2016
31
Chief Privacy Officer
Executive and Senior Management
Human Resources Department
IT Staff
Legal Department
Essay Writing Service Features
Our Experience
No matter how complex your assignment is, we can find the right professional for your specific task. Achiever Papers is an essay writing company that hires only the smartest minds to help you with your projects. Our expertise allows us to provide students with high-quality academic writing, editing & proofreading services.
Free Features
Free revision policy
$10Free bibliography & reference
$8Free title page
$8Free formatting
$8How Our Dissertation Writing Service Works
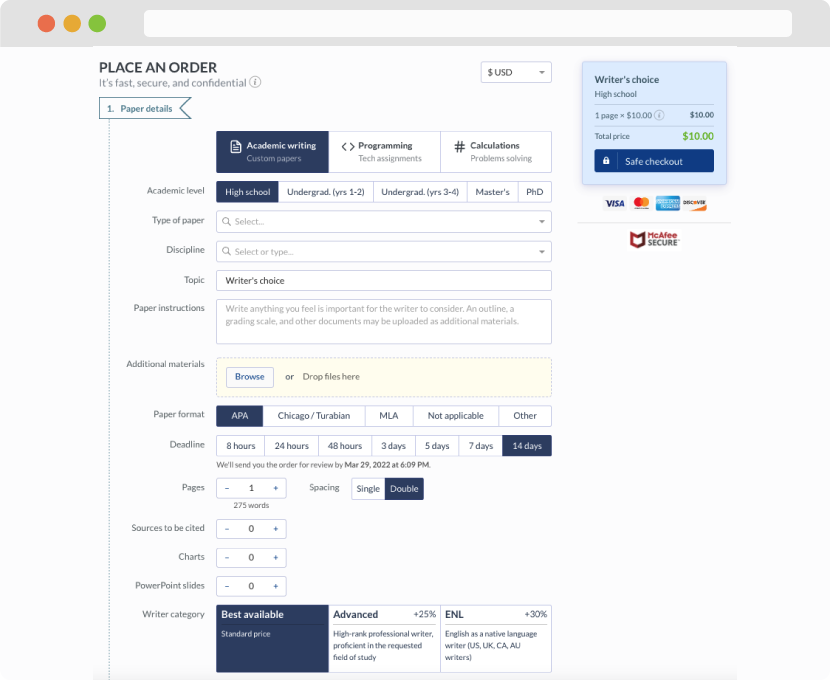
First, you will need to complete an order form. It's not difficult but, if anything is unclear, you may always chat with us so that we can guide you through it. On the order form, you will need to include some basic information concerning your order: subject, topic, number of pages, etc. We also encourage our clients to upload any relevant information or sources that will help.
Complete the order form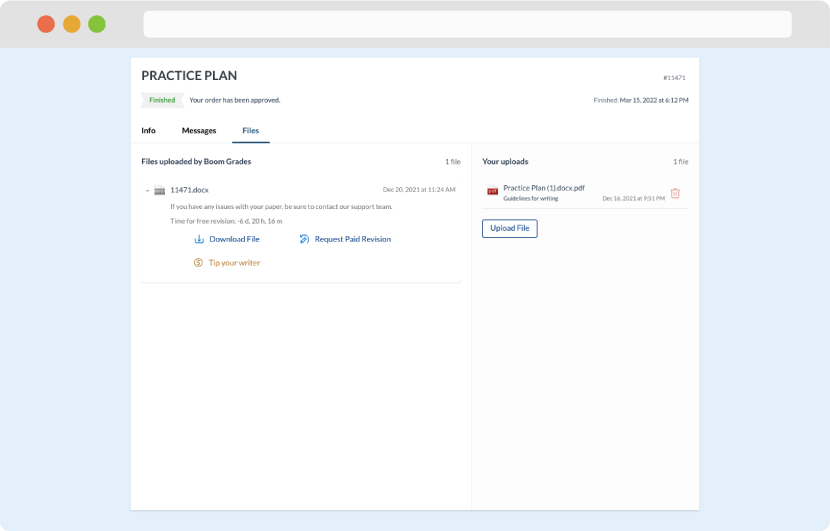
Once we have all the information and instructions that we need, we select the most suitable writer for your assignment. While everything seems to be clear, the writer, who has complete knowledge of the subject, may need clarification from you. It is at that point that you would receive a call or email from us.
Writer’s assignment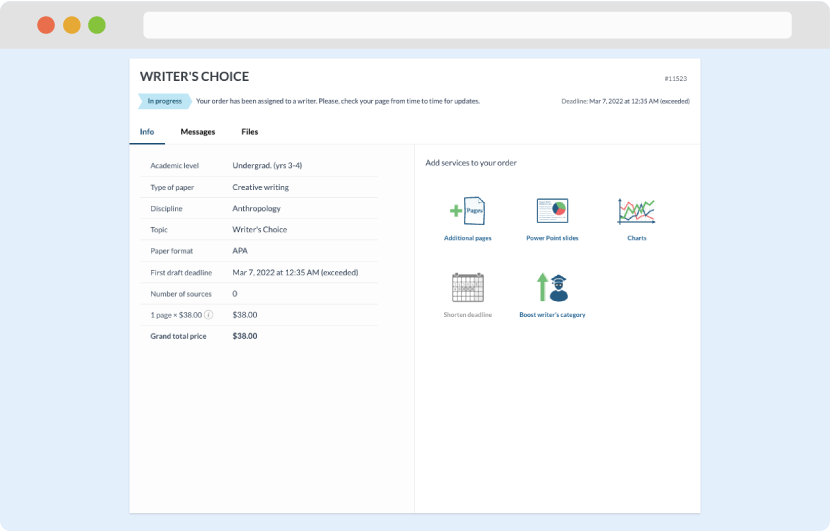
As soon as the writer has finished, it will be delivered both to the website and to your email address so that you will not miss it. If your deadline is close at hand, we will place a call to you to make sure that you receive the paper on time.
Completing the order and download